In the ever-evolving landscape of blockchain technology, the need for seamless interoperability between different networks has never been more pressing. As the crypto ecosystem expands, so does the demand for efficient, secure, and truly decentralized solutions to bridge the gap between disparate blockchains. Enter Xythum, a groundbreaking project that promises to revolutionize the cross-chain bridging space with its innovative approach to decentralization, security, and performance.
The Current Bridging Landscape: A Sea of Centralization
To appreciate the significance of Xythum, we must first understand the current state of cross-chain bridges and the challenges they face. The blockchain world is fragmented, with numerous networks operating in isolation. Cross-chain bridges emerged as a solution to this problem, allowing users to transfer assets and data between different blockchains. However, the majority of these bridges have opted for centralized architectures, sacrificing the core tenets of blockchain technology in favor of convenience and speed.
The Centralization Conundrum
Most popular bridges today rely heavily on centralized infrastructure. For instance, many top-tier bridges use cloud services like Google Cloud to run their nodes. This approach, while efficient, introduces a single point of failure and goes against the decentralized ethos of blockchain technology.
The reasons for this centralization are multifaceted:
- Performance Optimization: Centralized systems can often process transactions faster, as they don’t need to reach consensus across a distributed network.
- Simplicity of Implementation: It’s easier to set up and maintain a centralized system than to coordinate a decentralized network of nodes.
- Control and Upgradability: Centralized bridges can be upgraded and maintained more easily, allowing for quick fixes and improvements.
- Cost-Effectiveness: Running a centralized system can be more cost-effective in the short term, as it requires less infrastructure and coordination.
- Regulatory Compliance: Centralized bridges can more easily implement KYC/AML procedures and comply with regulatory requirements.
However, this centralization comes at a significant cost to security, censorship resistance, and true blockchain interoperability.
Common Centralized Bridging Strategies
Centralized bridges typically employ one of several strategies to facilitate cross-chain transfers:
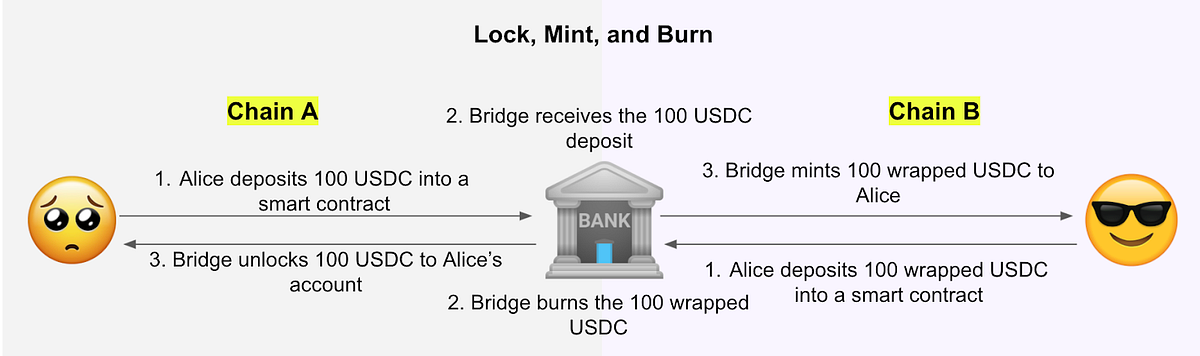
Lock and Mint: This is perhaps the most common approach. Here’s how it works: User sends assets to a smart contract on the source chain. The bridge detects this transaction and locks the assets. The bridge then mints an equivalent amount of wrapped assets on the destination chain. When bridging back, the wrapped assets are burned, and the original assets are unlocked.
While efficient, this method relies heavily on the bridge operator’s honesty and security. Atomic Swaps:
This method involves a simultaneous exchange of assets between two parties on different chains. It requires precise timing and coordination, often facilitated by a centralized intermediary.
Liquidity Pools:
Some bridges maintain liquidity pools on various chains. Users swap their assets into these pools on one chain and receive equivalent assets from the pool on another chain. This method can be faster but introduces liquidity risks and potential slippage.
Synthetic Assets:
- Instead of moving actual assets, some bridges create synthetic versions of assets on other chains.
- These synthetics track the price of the original asset but don’t represent actual ownership.
Each of these methods has its pros and cons, but they all share a common weakness: centralization. This centralization introduces various risks, including the potential for hacks, censorship, and manipulation.
The High Cost of Centralization: A History of Hacks
The centralized nature of many cross-chain bridges has made them attractive targets for hackers. The cryptocurrency space has witnessed several high-profile bridge hacks that have resulted in massive losses. Let’s examine some of the most notable incidents:
Ronin Network Hack (March 2022)
- Loss: $615 million in Ethereum and USDC
The Ronin Network, which powers the popular blockchain game Axie Infinity, suffered the largest cryptocurrency hack in history. A group of cybercriminals, believed to be associated with North Korea, managed to compromise the network’s validators and steal private keys. With these keys, they were able to authorize fraudulent withdrawals, making off with an enormous sum of cryptocurrency.
This hack highlighted the dangers of centralized control over bridge validators. Ronin operated with only nine validator nodes, five of which were enough to approve any transaction. The hackers managed to control four nodes and compromised an additional one run by Axie DAO, giving them the majority needed to authorize the fraudulent transactions.
Poly Network Hack (August 2021)
- Loss: $611 million (later returned)
The Poly Network hack was a unique case that exposed critical vulnerabilities in cross-chain protocols. The hacker exploited a flaw in the Poly Network’s smart contract code, specifically in how it handled transaction approvals across different chains.
Interestingly, the hacker claimed to have carried out the attack to expose the vulnerability and “keep the funds safe.” After negotiations with the Poly Network team, all funds were eventually returned. While this incident had a relatively happy ending, it underscored the potential for catastrophic losses due to smart contract vulnerabilities in centralized bridge architectures.
Wormhole Bridge Hack (February 2022)
- Loss: $326 million
The Wormhole bridge, which connects Ethereum and Solana, fell victim to a sophisticated attack that exploited a vulnerability in its signature verification process. The attacker managed to forge valid signatures, allowing them to mint 120,000 wrapped Ethereum tokens on Solana without actually locking up any ETH on the Ethereum side.
This hack was particularly concerning because it demonstrated how even well-audited bridges could have critical vulnerabilities. The centralized nature of the bridge’s guardian system meant that once the signature verification was bypassed, there were no additional layers of security to prevent the fraudulent minting of tokens.
Harmony Horizon Bridge Hack (June 2022)
- Loss: $100 million
The Harmony Horizon bridge, which facilitated transfers between Harmony and Ethereum, Bitcoin, and Binance Chain, was compromised when attackers gained control of the required two out of five multisig wallets needed to approve transactions. This allowed them to initiate and approve fraudulent transactions, draining the bridge of various cryptocurrencies.
The incident highlighted the risks associated with centralized multisig schemes, where compromising a small number of key holders can lead to catastrophic losses.
Nomad Bridge Hack (August 2022)
- Loss: $190 million (partially recovered)
The Nomad bridge hack was unique in its execution and scope. A fundamental flaw in the bridge’s smart contract allowed users to withdraw more funds than they had deposited. Once the initial fraudulent transaction was noticed, numerous copycats jumped in, leading to a “free-for-all” where anyone could exploit the vulnerability.
This incident showcased how quickly a vulnerability in a centralized bridge can spiral out of control, leading to massive losses in a very short period.
Multichain (Anyswap) Hacks Multichain (formerly Anyswap) has suffered multiple hacks:
- July 2021: $7.9 million lost due to compromised MPC keys
- July 2023: $126 million lost, again due to compromised keys
These recurring incidents with Multichain highlight the ongoing risks associated with centralized key management in bridge architectures.
The Fallout
These hacks have had severe consequences for the crypto ecosystem:
- Financial Losses: Collectively, these hacks have resulted in losses exceeding $2 billion, affecting both individual users and the broader crypto market.
- Reduced Trust: Each major hack erodes trust in cross-chain solutions, potentially slowing down the adoption of blockchain technology.
- Regulatory Scrutiny: These high-profile incidents have drawn increased attention from regulators, potentially leading to stricter oversight of the crypto industry.
- Market Volatility: Large-scale hacks often lead to significant market turbulence, affecting the value of cryptocurrencies across the board.
- Innovation Challenges: The fear of hacks can stifle innovation, as developers and investors become more risk-averse.
These incidents serve as a stark reminder of the vulnerabilities inherent in centralized bridge architectures and underscore the urgent need for more secure, decentralized solutions.
Beyond Hacks: The Hidden Dangers of Centralized Bridges
While hacks grab headlines and cause immediate, quantifiable damage, they’re not the only concern with centralized bridges. There are other, more subtle risks that users face when interacting with these platforms:
Centralized bridges, by their very nature, have privileged access to user transaction information before it hits the blockchain. This opens up opportunities for malicious actors within the bridge operation to engage in front-running or sandwich attacks.
-
Front-Running:
- Bridge operators can see incoming large transactions.
- They can then place their own transactions ahead of the user’s, profiting from the price movement caused by the large trade.
-
Sandwich Attacks:
- A more sophisticated version of front-running.
- The attacker places one transaction just before the victim’s transaction and another just after.
- This allows them to profit from both the price increase and decrease caused by the victim’s large trade.
For example, consider a user wanting to bridge a large amount of ETH to another chain. A malicious bridge operator could:
- See the incoming transaction
- Quickly buy the receiving asset on the destination chain
- Let the user’s transaction go through, causing the price to rise
- Sell the asset at a profit
While not all bridges engage in such practices, the centralized nature of many bridges makes it possible and very difficult to detect
Lack of Transparency
Centralized bridges often operate as black boxes. Users have little insight into:
- How their assets are actually being transferred
- What happens to their assets while in transit
- The true liquidity backing wrapped assets
This lack of transparency can hide inefficiencies, potential vulnerabilities, or even malicious activities.
Censorship Risks
Centralized bridges can potentially censor or block transactions based on various factors:
- Geographical location of the user
- Pressure from regulatory bodies
- Source or destination of funds
This goes against the ethos of blockchain technology, which promises permissionless and borderless transactions.
Single Points of Failure Centralized bridges often rely on a small set of validators or a single entity to operate. This creates single points of failure that can be exploited by attackers or simply fail due to technical issues.
Liquidity Risks Some centralized bridges use liquidity pools to facilitate quick transfers. However, these pools can be drained during periods of high volatility or large withdrawals, leaving users unable to bridge their assets when they need to most.
Potential for Exit Scams In the worst-case scenario, the operators of a centralized bridge could potentially abscond with user funds in an exit scam. While reputable projects are unlikely to do this, the mere possibility introduces an element of counterparty risk that shouldn’t exist in truly decentralized systems.
Xythum: A Paradigm Shift in Cross-Chain Bridging
In the face of these challenges, Xythum emerges as a beacon of innovation, promising to deliver what many thought impossible: a truly decentralized cross-chain bridge that doesn’t compromise on speed, cost-effectiveness, or security. Let’s dive deep into what makes Xythum a game-changer in the world of blockchain interoperability.
The Xythum Vision: Decentralization Without Compromise
At its core, Xythum is built on the principle that decentralization shouldn’t come at the cost of performance or user experience. The team behind Xythum recognized the fundamental flaws in existing bridge architectures and set out to create a solution that addresses these issues head-on.
Key pillars of Xythum’s vision include:
- True Decentralization: Unlike many “decentralized” bridges that still rely on centralized components, Xythum aims for complete decentralization from the ground up.
- Uncompromising Security: By leveraging cutting-edge cryptographic techniques, Xythum provides robust security without relying on centralized custodians or validators.
- Speed and Efficiency: Xythum proves that decentralization doesn’t have to mean slow transaction times or high costs.
- Cross-Chain Compatibility: The platform is designed to work seamlessly across a wide range of blockchain networks, including Bitcoin, Ethereum, Solana, and more.
- Privacy-Preserving: Through innovative use of zero-knowledge proofs and other privacy-enhancing technologies, Xythum protects user privacy without sacrificing transparency.
The Technology Behind Xythum
Xythum’s revolutionary approach is made possible by a combination of advanced technologies and innovative cryptographic techniques. Let’s break down the key components that power this next-generation bridge:
1. Schnorr Signatures: The Foundation of Efficiency
At the heart of Xythum’s efficiency lies the use of Schnorr signatures. This signature scheme offers several advantages over the more commonly used ECDSA (Elliptic Curve Digital Signature Algorithm):
- Linearity: Schnorr signatures are linear, allowing for easy aggregation.
- Smaller Size: They require less space on the blockchain, reducing transaction costs.
- Faster Verification: Schnorr signatures can be verified more quickly, speeding up transaction processing.
Compared to traditional ECDSA signatures, Schnorr signatures offer up to 40% less computation, translating directly into faster and cheaper transactions for Xythum users.
2. Signature Aggregation: Scaling Decentralization
One of the key innovations in Xythum is its use of signature aggregation. In traditional multi-sig setups, each validator would need to submit their signature separately, leading to higher costs and slower processing times as the number of validators increases.
Xythum solves this by aggregating all validator signatures into a single signature. This means that regardless of how many validators are securing the network, only one signature needs to be submitted and verified on-chain. The benefits are profound:
- Lower Costs: Dramatically reduced on-chain footprint leads to lower transaction fees.
- Faster Processing: Single signature verification is much quicker than verifying multiple signatures.
- Scalable Decentralization: The network can increase the number of validators without impacting performance or costs.
3. FROST: Flexible Round-Optimized Schnorr Threshold Signatures
FROST (Flexible Round-Optimized Schnorr Threshold Signatures) is a cutting-edge protocol that Xythum employs to achieve rapid consensus among its decentralized network of validators. Key features of FROST include:
- Single-Round Signing: FROST allows for signature aggregation in a single round of communication, drastically reducing latency.
- Threshold Security: It implements a t-of-n threshold scheme, where any subset of t validators out of n total validators can produce a valid signature.
- Asynchronous Operation: Validators can operate asynchronously, improving resilience and reducing coordination overhead.
The implementation of FROST enables Xythum to achieve sub-second bridging speeds while maintaining a high level of decentralization and security.
4. Sharding and Parallel Processing
To further enhance performance, Xythum implements a sharding mechanism that allows for parallel processing of transactions:
- Validator Sharding: The network of validators is divided into shards, each responsible for a subset of transactions.
- Parallel Execution: Different shards can process transactions simultaneously, greatly increasing throughput.
- Dynamic Load Balancing: The system can dynamically adjust shard allocation based on network load, ensuring optimal performance at all times.
This sharded architecture, combined with FROST’s asynchronous signing capabilities, allows Xythum to scale horizontally, handling a growing number of cross-chain transactions without sacrificing speed or decentralization.
5. Zero-Knowledge Proofs and Privacy Enhancements
Xythum incorporates advanced zero-knowledge proof systems, Trusted Execution Environments and SXG to enhance privacy and security:
- Proof of Validity: Zero-knowledge proofs are used to verify the validity of cross-chain transactions without revealing sensitive details.
- Confidential Transactions: The amounts and types of assets being bridged can be kept confidential, protecting users from potential front-running or targeted attacks.
- Secure Enclaves: Critical computations are performed within secure hardware enclaves, isolated from the rest of the system.
- Attestation: TEEs provide cryptographic proof that the correct code is being executed, enhancing trust in the bridge’s operations.
- Key Protection: Sensitive cryptographic keys can be securely managed within the TEE, reducing the risk of key compromise.
- Data Authenticity: SXGs allow for the cryptographic signing of data exchanged between chains, ensuring its authenticity.
- Replay Protection: The use of SXGs helps prevent replay attacks, where valid transactions are maliciously repeated.
Xythum’s Approach to Speed and Cost
Despite offering advanced features and robust security, Xythum manages to be one of the fastest and most cost-effective bridging solutions available. This is achieved through a combination of technological innovations and clever design choices:
Parallel Processing:
The sharded architecture allows for multiple transactions to be processed simultaneously. This dramatically increases throughput without sacrificing decentralization.
Efficient Cryptography:
- The use of Schnorr signatures and aggregation reduces the computational overhead for transaction verification.
- This translates to faster processing times and lower costs. we opt to use onChain cheap options like taproot addresses for bitcoin.
- use of aggregated signatures makes transactions lightweight accross chains hence cheaper.
Optimized Consensus:
The FROST protocol enables rapid consensus among validators with minimal communication overhead. This allows for sub-second finality times for most transactions.
Batching and Netting:
Where possible, transactions are batched and netted to reduce the number of on-chain operations required. This is particularly effective in combination with the dark pool functionality.
Conclusion: Xythum - Bridging the Future of Blockchain
As we’ve explored in this deep dive, Xythum represents a quantum leap forward in the world of cross-chain interoperability. By combining cutting-edge cryptographic techniques, innovative architecture, and a unwavering commitment to decentralization, Xythum has created a bridge that is not just a marginal improvement over existing solutions, but a fundamental reimagining of what’s possible in this space.
As the blockchain landscape continues to evolve, with new chains and layer 2 solutions emerging regularly, the need for robust, secure, and efficient cross-chain bridges will only grow. Xythum is not just meeting this need – it’s setting a new standard for what users and developers should expect from cross-chain infrastructure.